Stolen data and fake accounts are an ever greater challenge and more topical than ever in the digital world. More and more new data leaks are being reported, millions of data records with names, account data or access data of customers are flowing into the hands of cyber criminals. Many media outlets are reporting on this, for example Handelsblatt or Der Spiegel. Artificial intelligence is reaching whole new levels, which also help criminals to carry out ever more skillful attacks. The damage to companies is immense and mostly lasting. On the one hand, through the direct financial damage, and on the other hand, through the lasting loss of trust of the customers towards the content of the providers.
Three different methods can protect companies from this type of cybercrime:
- “Human checks,” such as captchas and other verification mechanisms in the user experience, have been developed to secure account creation and interactions on platforms, in communities, and with companies. Artificial intelligence, however, can already overcome simple “human checks” by mimicking the required behavior of humans. Be it reading graphical elements or answering computational tasks. The implications for companies can be serious.
- “Background checks” via databases or algorithms are designed to confirm the authenticity of interactions in the background. Current characteristics of the transaction combined with analysis of past data and behaviors lead to an assessment. With associated probabilities and residual risks, it is confirmed whether a transaction can be classified as authentic. Used data points, processes and decision logics are thereby little transparent to the customer and in the end it is a contest between protection and abuse by artificial intelligences.
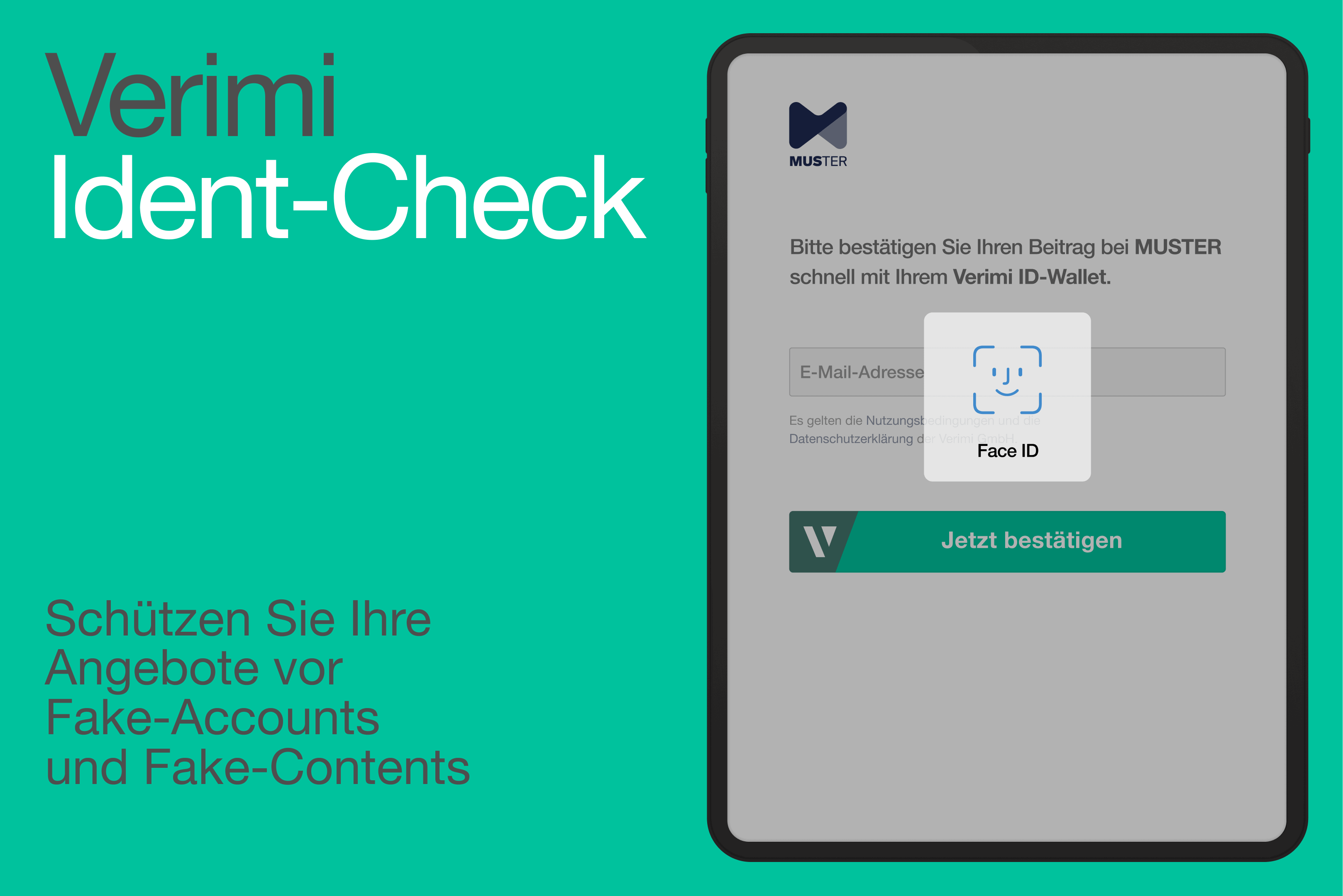
- “Direct authentication” of a transaction by the customer already yields the highest security in security-relevant and regulated use cases. For example, in banking. However, so-called transaction signing has not been user-friendly: customers often needed special apps to do this, such as the bank’s push TAN app. ID wallets change this: They combine the high level of security with the simplest user experience – and they can be used across many applications and many providers. ID wallets thus make new solutions possible that are highly attractive for e-commerce companies, networks and content platforms. A simple “ident check” with an ID wallet verifies human users reliably and quickly.
In this blog post, we’ll consider the challenges businesses face and give you expert tips on how to successfully navigate this situation. The challenges for businesses are clear:
- Fake accounts are difficult to identify: Detecting fake accounts becomes a difficult task for businesses because bots with artificial intelligence can imitate human behaviors and profiles. Fake accounts may increase user numbers in the short term as a KPI, but in the long term they destroy the quality of the offering.
- Fake content burdens the real community: Poorly protected platforms are increasingly flooded with misleading or irrelevant content. Filtering out this content after the fact requires a great deal of effort. Fake content burdens the real community and leads to a loss of trust and ultimately disinterest among users.
- Lower relevance for advertising partners reduces marketing potential: The loss of trust among users and the dilution of the user group also reduce the relevance of the platform for commercial partners. Marketing frequency thus becomes increasingly difficult.
- Stolen identity and payment data lead to direct damage: Stolen identities, for example names with IBAN or usernames with passwords, can be used to directly trigger payment-related transactions. In the end, the damage often remains with the e-commerce provider.
From lasting loss of trust to direct financial damage – companies have a great interest in protecting themselves early on against fake accounts, fake content and fraud through stolen identities and payment data. Here’s how you can protect yourself:
- Verify during account creation: bots powered by artificial intelligence are creating fake accounts on a large scale. Make sure accounts on your platforms are created by “real people.” Weigh whether simple technologies are sufficient for your offering or whether you need secure methods without adding complexity, especially if users can post their own content on your platform.
- Verification in content creation: Leaked credentials are increasingly being used to take over existing accounts by criminals. For sensitive interactions and transactions from existing customers, make sure it is the legitimate user. Use the simplest possible procedures that are seamlessly integrated into the user flow and do not compromise the user experience.
- Verification at payment: Suspicious transactions from stolen account and identity data can be filtered through background checks. This can be costly and involve high integration and transaction costs – and residual risks always remain. Check to see if there are simpler processes that can achieve better results for your business with less effort.
- Interact with the customer: Actively involve your customers in transaction verification. This saves time-consuming background processes and residual risks. Clarity and transparency also convey an important message very directly: “We value security” – be it in content or payment.
Artificial intelligence will be able to take on more and more tasks – both for security and for cybercriminals. Just as digital payment data and identity data will flow off in ever new leaks, AI will also overcome indirect and data-driven safeguards faster and faster in the future. Security-related and regulated use cases show that asking users to authenticate themselves provides the highest level of security. ID wallets now combine the high level of security with the simplest user experience.
Verimi offers a simple and familiar user experience for the ID check with the ID Wallet: short log-in or Face ID, confirm transaction, done. At the same time, this makes the positioning to the user very visual: “We value security and trust!” This saves elaborate explanations of why the content is authentic – the user has experienced it himself! Identification is based on the verified personal attributes from the Verimi ID wallet – be it the verified ID card, passport or driver’s license. Or the confirmed access to the bank account. A variety of combinations allows the statement “It’s a real person!”. Quick and easy for the customer. Highly efficient for companies.