Customers increasingly have to identify themselves digitally – to log in to many portals, to use services, to pay, to open accounts and securities accounts or to sign digitally. It is very important for companies to integrate suitable and secure identification procedures: For each use case, the customer’s identity must be verified as securely as necessary and as conveniently as possible.
What procedures are there for digital identity verification, how do the identification procedures differ and what do companies need to bear in mind?
Here is the most important information!
What is identity verification?
An identity check ensures that a person really is who they claim to be. As a rule, a physical ID document (ID card, passport, residence permit or similar) is checked for authenticity and the photo on the ID is compared with the actual person. This can be done physically on site or via online channels. In addition, there are already the first online identification procedures that no longer require physical ID documents at all, but instead access verified digital data.
Why do companies verify identity at all?
On the one hand, there are companies that have to verify the identity of their customers due to regulatory requirements. On the other hand, companies themselves decide to verify their customers’ identities due to the requirements of their business models. In addition, more and more legally binding contracts are being concluded online – the identity of the signatory must be ensured for the legally binding digital signature.
The regulatory requirements are very clearly formulated, for example by the Federal Financial Supervisory Authority (BaFin) or the Federal Network Agency (BNetzA). The companies that have to comply with these regulations are aware of these requirements. Non-regulated companies decide for themselves how to establish their identity. Possible motives include combating fraud when placing orders and making payments, protecting personal data when accessing service portals or verifying identity and driving licenses, for example in the case of car sharing.
Identification vs. authentication – what’s the difference?
Many people are already familiar with the term “identify” as “prove your identity”. This means that a person proves their own identity, e.g. by presenting an official ID document. Above all, identifying means proving your identity for the first time, i.e. on your first visit or first contact, when opening a business relationship, opening an account or accessing a service portal.
“Authentication” is more familiar to many than “logging in”. It refers to the confirmation of access authorization based on the already verified identity data. The aim here is to be able to come back easily after the initial identification, for example to log into online banking or the service portal. To do this, it must be ensured each time that exactly the same customer logs in as the one who identified themselves – without having to re-identify themselves each time.
Everyone is talking about ID wallets being the future – why?
Identify yourself once and then log in again and again: This seems clear and simple for any service portal or bank account. However, the more accounts and portals customers use, the more tiring it can become: Always having to re-identify, always different logic to log in. Forgotten passwords, blocked access, calls to the service center, re-identification or even new PIN letters are the result – this is inconvenient for the customer and expensive for companies.
ID wallets offer a solution to this problem: users store their ID data once in their ID wallet and can then use this data anywhere – because the user then releases their ID data depending on the application. With an ID wallet, the user experience is more like ‘logging in’ than ‘identifying’ – making it much faster and more convenient. And for companies, ID wallets significantly lower the barriers to entry for new customers. It’s similar to paying online: You can re-enter your credit card details every time, or you can enter them once with a payment service and use that payment service to authorize all future payments. Everyone knows that this is both much easier and much more secure than giving your credit card details directly to every provider.
However, even to create an ID wallet, the user must identify themselves online once, i.e. use an identification procedure. In the same way that you have to deposit your credit card once at the start of an online payment service or mobile payment. It is therefore important to know which online identity verification procedures are available. In addition, the spread of ID wallets still takes time, which is why many companies still integrate identification procedures directly as “one-time ident” or “silo ident” – just as you can often still pay with a credit card. In this case, you still have to enter all the data again each time.
How can you verify an identity online?
The challenge with online identity verification is that the customer is not on site to present their ID document. The authenticity of the ID document and the comparison of photo and person can therefore not be carried out physically by appropriately trained employees on site.
This is why there are numerous identification procedures that make it possible to carry out an identity check via the Internet, i.e. online. This means that the necessary identification can be tailored much more flexibly to the customer’s wishes and situation than if the customer had to appear in person. This usually leads to a very positive customer experience. High customer satisfaction and low abandonment rates are key objectives.
Why should you offer different procedures for digital identity verification?
Different customers have different life situations, needs and expectations. A single procedure will not be able to cover all needs and expectations. Some processes are very easy to use for some customer groups, while others offer a wider customer reach but tend to represent the “lowest common denominator” in terms of customer experience. A selection ensures the best possible experience for all different customer groups. Three factors are central to the mix of methods:
- Fewer cancellations
There is a risk that customers will cancel the identification process – even before it starts or during the process. The reasons are numerous and specific to each procedure offered, as our list below shows. If the customer has a choice, they can use the process that best suits their current circumstances. - Higher conversion
Once the customer has decided on a process, it must be as quick and easy as possible for them to implement – this is about interaction and user guidance, rather than the number of screens or the actual processing time. Abortions due to technical factors, handling problems or response times must be avoided. If the customer changes their selection decision again, it must be possible to switch to a different process. - Lower costs
The transaction costs of the individual Ident method are usually disproportionate to the value of the desired customer relationship. If a customer cancels the onboarding process because of the ident requirement, this has a significant impact on the overall customer acquisition costs. Ident procedures have very different costs and therefore a good mix of offers is relevant in order to acquire many customers.
Can I compare the performance of Ident procedures?
Unfortunately not. Each process must be considered in the context of the specific use case. Three simple examples:
- A customer has invested a lot of time filling out their tax return online. Will he now end the process because of the necessary identification procedure and submit his tax return differently?
- A customer wants to pay by direct debit, enters their account details and the provider requires confirmation of identity to protect against misuse. Will he rather identify himself with his online banking or with his identity card?
- One customer finds the innovative AutoAbo offer exciting. He configures a vehicle and a subscription; the last step is the digital signature. The customer stops at the Ident for the digital signature – is this due to the Ident procedure?
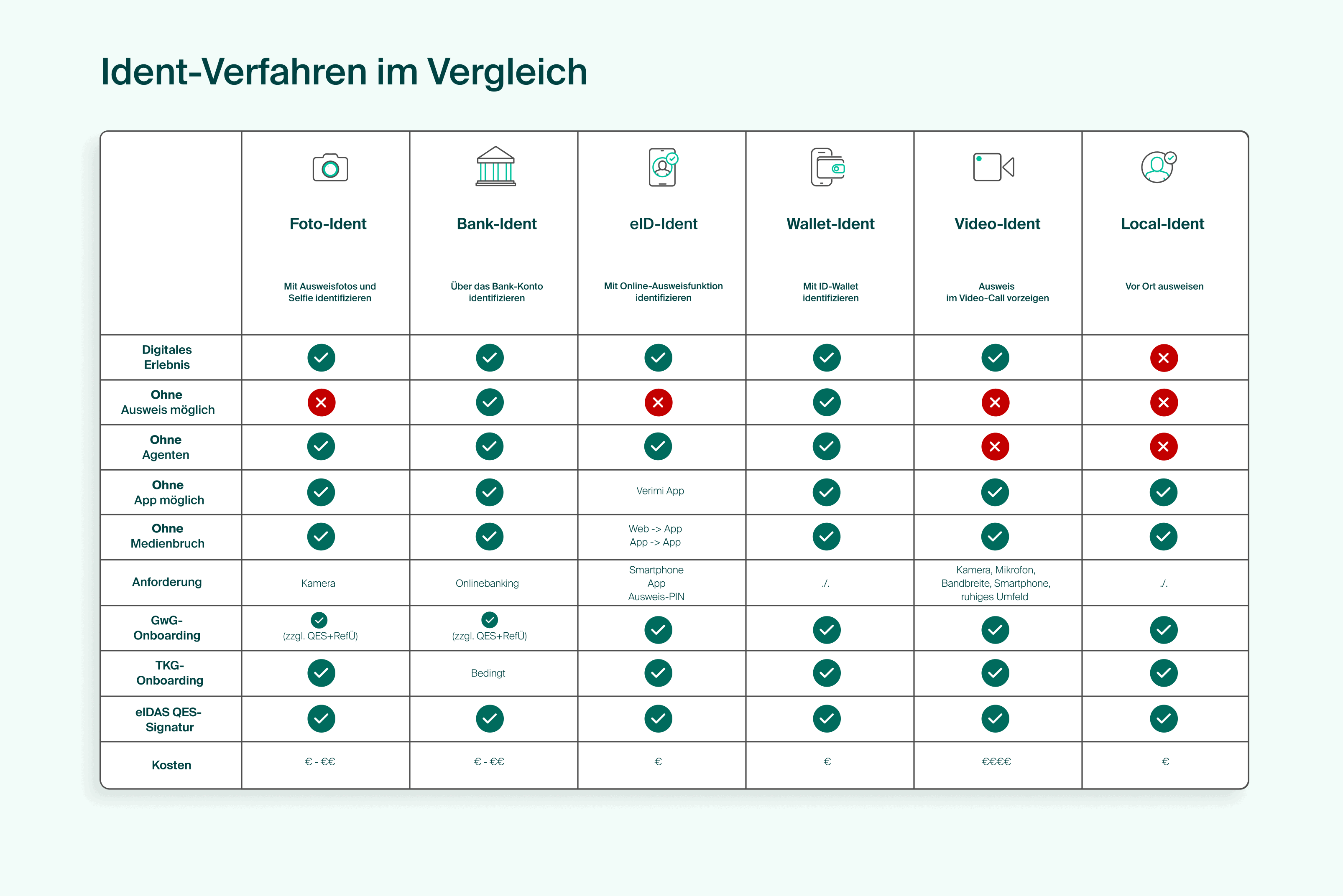
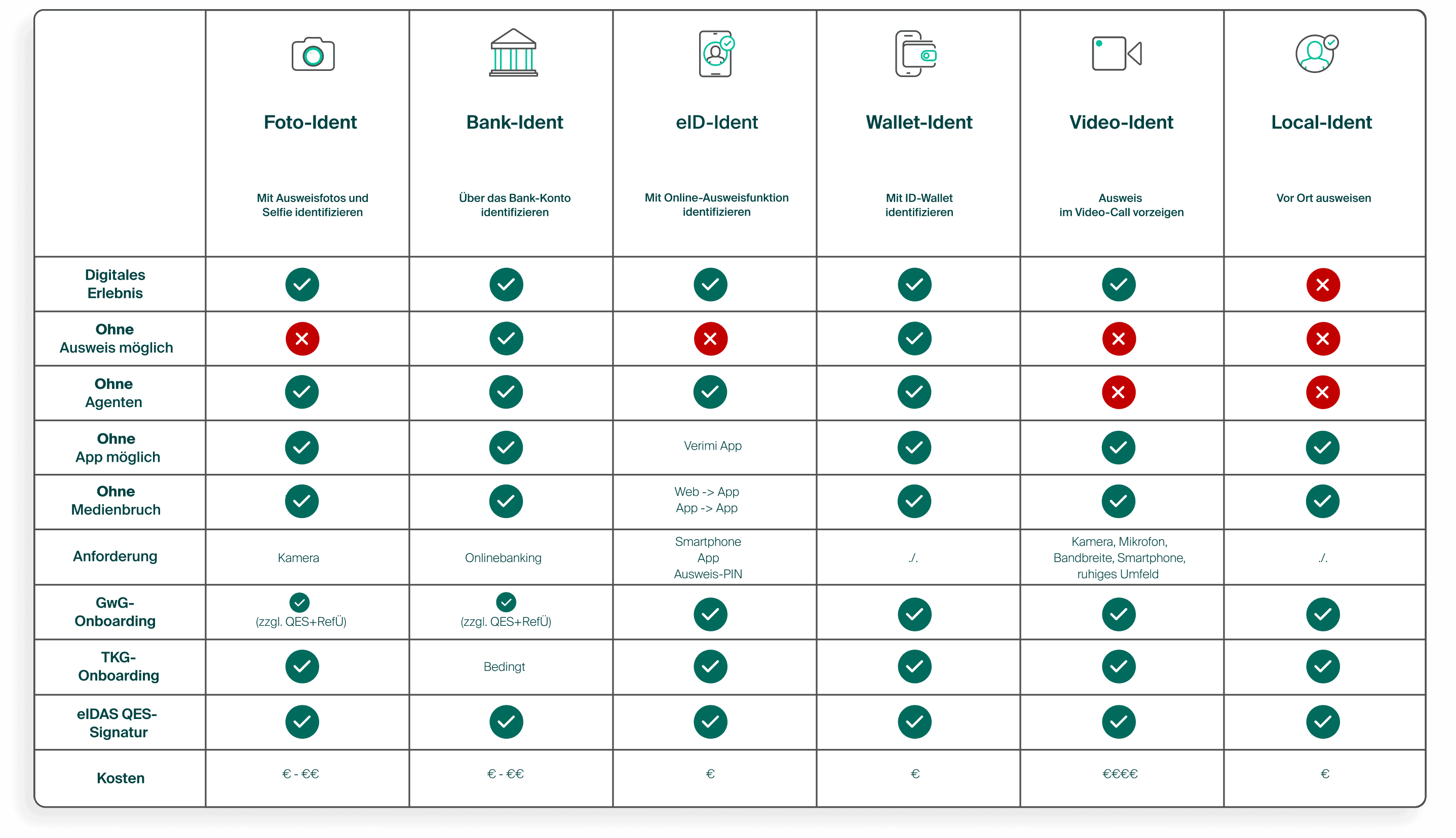
What different identification methods are there?
There are various possible combinations of identification procedures for each application. A key criterion for the selection is whether it is a regulatory relevant identity verification (e.g. for banks, telecommunications, gambling, sports betting, public administration or for digital signatures) or whether specific – but unregulated – requirements of a company need to be considered for identity verification (e.g. onboarding for a service portal, exclusion of misuse, validation of payment data, access verification, driver’s license verification, etc.). It is also clearly defined which Ident methods are suitable for confirming identity for a digital signature.
Basically, there are 6 standard identification methods, whereby there are relevant variants and adaptations for each identification method according to the specific requirements from the use cases – and there may be further secure adaptations in the future:
- Identification with the online ID card (eID-Ident)
With the online ID card procedure, customers can read their German ID card using a suitable app via the NFC interface of their smartphone by entering their ID card PIN.
- What does the customer need: A German ID card, a smartphone with an app for reading the ID card (e.g. Verimi app) and their eID PIN.
- What is the user experience like: The user downloads an app (e.g. the Verimi app), opens the app and selects the function. They then hold their ID card up to the NFC antenna of their smartphone twice and enter their ID PIN in between.
- What is it suitable for? The online ID card is suitable for all use cases, both regulated and non-regulated. The identity can be used to trigger a digital signature (QES).
- What are the costs: The Ident procedure with the OnlineAusweis is relatively inexpensive in terms of transaction costs.
- What can be said about the procedure: The OnlineAusweis is a procedure for ‘connoisseurs’. Unfortunately, it is not widely used, less than 20% of Germans use the eID function – but those who know and use the eID function are generally happy to do so. For broad acceptance, the online ID card has some challenges, e.g. customers must have an app, know the position of the NFC antenna on the smartphone, hold the ID card correctly to the smartphone twice, know and enter their PIN, etc. Use is also limited to German ID cards.
2. Identification with online banking access (Bank-Ident)
With Bank-Ident, customers use their personal online banking access to identify themselves. The identity data already checked and stored by the bank is used; the transaction data from the bank account is irrelevant.
- What the customer needs: online banking access. Whether via smartphone or via the web. The customer does not need a physical ID card!
- What is the user experience like: The user selects their bank interactively during the process, logs into their online banking and confirms their identification. Done.
- What is it suitable for: Bank-Ident is flexible for a great many applications. It can simply confirm access to the bank account (e.g. fraud prevention for online payments), confirm identity data (e.g. portal access), trigger a digital signature (QES) or even be used in regulated applications, e.g. for onboarding in compliance with the Money Laundering Act.
- What are the costs: The Bank-Ident procedure is a very cost-effective procedure in its basic form, as it accesses data that has already been digitally recorded. However, as requirements increase (e.g. QES triggering, AMLA compliance), additional modules are added to the process and costs rise as a result.
- What can be said about the process: The major advantage of Bank-Ident is that the customer does not need to have an ID card to hand! It is therefore fully digital and very easy to use from anywhere and spontaneously! Bank-Ident is very easy to use for customers who use their online banking and also want to use it for identification purposes. Not all Germans use online banking yet and, depending on the application, the bank account must be in Europe (Sepa) or Germany.
3. Identification in a video call (Video-Ident)
With Video-Ident, the customer makes a video call with a trained agent.
- What the customer needs: The customer needs their ID document and suitable hardware to be able to make a video call (including a camera, microphone, bandwidth), a cell phone to receive a text message and a quiet environment. Depending on regulatory requirements, they may need to be alone in a room, for example.
- What is the user experience like: The customer confirms that their hardware is suitable for the video call, waits for the call agent and then makes the video call. At the end, an SMS TAN is usually entered for confirmation. In many cases, the provider also requires the download of an extra Ident app to ensure video quality and access to hardware components (camera, flash, microphone).
- What is this suitable for? Basically for a great many applications up to and including digital signatures and money laundering compliance. However, it is a very time-consuming and costly process that is prone to faults and should only be used very selectively in the sense of a ‘fall-back’.
- What are the costs: Video-Ident is a very expensive process. For identification, a video agent is tied up for several minutes, the availability of the agents must be guaranteed and the agents must generally be well trained, and high demands are placed on the trustworthiness of agents and job security. This explains the costs.
- What can be said about the process: Video-Ident has many challenges, e.g. limited service times from morning to evening, long waiting times until the call agent answers the call, especially at peak times, long call times of sometimes over 10 minutes and often ‘personal’ topics from the individual customer dialog – be it linguistic or interpersonal factors. Added to this are possible disconnections or other disruptions during the video call. At the same time, the personal dialog and moderated user guidance make it understandable for many customer groups.
4. Identification using an ID photo and selfie (photo ID)
Photo-Ident uses artificial intelligence (AI) to confirm identity using photos of the ID document in combination with a selfie. As a rule, instead of just photos, short video sequences are actually recorded and analyzed to check factors such as authenticity and vitality. Various precautions further strengthen security, e.g. location detection, IP address verification, exclusion of multiple use, etc.
- What does the customer need: The customer needs their ID document and suitable hardware to be able to take photos and a selfie (e.g. smartphone or laptop).
- What is the user experience like: The customer takes photos of the front and back of their ID document as well as a selfie. The process can also be supplemented with short voice sequences or moving images to accompany the selfie.
- What is this suitable for? A great many quick and simple applications are possible, in principle Photo-Ident is also suitable for digital signatures, and in combination with a reference transfer (similar to Bank-Ident) also for money laundering compliance.
- What are the costs: Photo-Ident is a very efficient process. Depending on the requirements for the data read out and the results, checks can be added, including background checks by agents. The costs vary accordingly.
- What can be said about the process: Photo-Ident is fast, simple and intuitive – at the same time, it requires the physical ID document and some handling to take the photos, which can be difficult in some situations. Yet it reaches many customer groups.
5. Identification directly at the point of sale (Local-Ident)
Traditionally, identification takes place on site. In order to be able to use the result online afterwards, the trained agents on site confirm the data in electronic systems. Many companies carry out these procedures for their own purposes in their own branches. In Germany, for example, there is the Post-Ident procedure, in which the customer’s identity is verified on behalf of another company. The procedure in our own branches is described here.
- What does the customer need: The customer needs their ID document and must be in the branch.
- What is the user experience like: The customer shows their ID document to the trained agent. The agent takes care of the actual identification process.
- What is it suitable for: Basically for a great many applications up to and including digital signatures and money laundering compliance. In particular, the digital identity captured in this way enables subsequent signatures (e.g. for purchase contracts, leasing contracts, general terms and conditions, consents, etc.) to be efficiently completed digitally as a QES batch signature.
- What are the costs: Local-Ident is efficiently supported by software. Hardware requirements must be met. The main expense is due to the deployment of the trained agent.
- What can be said about the process: Local-Ident is a classic on-site process that can be used well if the customer is in the branch anyway and needs to be identified in compliance with regulations. In particular, Local-Ident replaces the traditional “making a copy of an ID card” and thus solves the handling and compliance challenges of branch operations.
6. Identification with an ID Wallet (Wallet-Ident)
The customer stores their verified ID data once in the personal ID Wallet – so that they can then retrieve it very easily when needed. The verified data is stored using one of the above-mentioned identification methods. The user experience for identification with the ID Wallet is then more like “authentication” (log-in) than “identification” (ID card):
- What does the customer need: the customer needs online access, whether via smartphone or via the web. They do not need a physical ID document!
- What is the user experience like: The customer logs into their ID Wallet and confirms that their verified identity data will be transmitted to the partner.
- What is it suitable for: In principle, the Wallet-Ident is suitable for all use cases that also reach the Ident procedures through which the ID data was placed in the wallet.
- What are the costs: The Wallet-Ident is very efficient, as the already verified digital data is retrieved. In addition to the costs of the process, the high conversion is particularly relevant, as there are no reasons for abandonment due to the handling of ID cards
- What can be said about the process: Wallet-Ident is an innovative process that belongs to the future. Users don’t want to have to show their ID again and again, but want to identify themselves directly online or with their smartphone – just as they leave their physical credit card at home when making mobile payments. Incidentally, every Verimi identification procedure automatically goes hand in hand with Wallet-Ident – if the user has already used Verimi before, they can automatically use their Wallet-Ident with any partner.
Graphic with comparison of the Ident procedures
Which is the best identification procedure?
Wallet-Ident is fundamentally superior to all single-use identification procedures. This applies above all to customer experience, conversion and costs. However, the challenge is that ID Wallets are still not widely used in practice in Germany.
For single-use ID procedures, it is important to consider the specific use case and define the right mix. To do this, it is important to analyze the individual case with experts before deciding on an actual mix of ID procedures.
Verimi combines Wallet-Ident and One-Time-Ident in a unique way: With the one-time ident at the partner companies, customers create their personal ID Wallet directly at Verimi. With each subsequent Ident, Verimi automatically checks whether the user can use their Wallet-Ident. This ensures that customers of Verimi partners are always offered the best possible experience.
The future of digital identification procedures
The ID of the future is the smartphone – just as the smartphone has already become the music player, the camera, the calendar, the messenger, the newspaper, the plane ticket, the admission ticket, the credit card and so much more. There is no doubt about it. The ID of the future will be accessible via an ID wallet on the smartphone. This ID wallet is a secure environment, hardly comparable with today’s IOS/Android wallets, where tickets, flight tickets, membership cards, etc. are stored. Much more comparable to the mobile payment infrastructure, where the reference to the credit card account is mapped in a highly secure manner.
In addition to the ID card, the ID Wallet will in future include other official attributes, at least the driver’s license, as well as official training and qualification certificates. This will enable further end-to-end digitization of business transactions in connection with ID Wallets. One of the drivers of this development is the EU’s mandatory EUDI wallets. The widespread use of ID Wallets will change the significance of ‘one-time ID procedures’ and ‘silo ID procedures’ – a change that will take time. In addition to the technical implementation, data sources and data recipients will also have to adapt to the new possibilities.
It will also take some time for customers and users to incorporate the new possibilities of ID wallets into their habits. In any case: “Convenience wins!” – and mobile payment shows how quickly a convenient method can conquer customers’ everyday lives. A situation in which the customer has to bring their physical ID into the digital world again and again for every application will not be sustainable in the long term. The development in mobile payment is a clear blueprint for this and shows that companies need to prepare for the new solutions at an early stage.
For companies, this means that ID Wallets will be an increasingly relevant addition to identification procedures in the coming years – for customers in the sense of a further, perhaps leading, selection option. For companies, to improve the costs and conversion of identification procedures. The inefficiency of “single-use IDs” is obvious; every company has to pay the production costs of a digital identity all over again. Many companies face the same challenge; a network for accessing customers’ existing digital identity data makes a lot of economic sense. It is therefore important for the future to offer a mix of identification procedures, which also includes ID Wallets in particular.
As digitalization progresses, it will become increasingly important to back up customer relationships and interactions in the digital space with identification and verification. In addition, transactions are increasingly being digitized end-to-end, which requires legally binding contracts using digital signatures – which in turn are based on digital identities. Existing and new use cases will have to increasingly incorporate identification procedures in order to reduce the risk of misuse in cyberspace. This applies to all areas: Payment transactions, eCommerce, personal data, mobility, etc. Fast, seamless and flexible solutions are important to keep conversion rates and customer satisfaction at a high level – high security and reliability of offers will become an increasingly important success factor in the digital world.